The Threat on Your Desk: Building an Evil USB-C Dock
Background#
In recent years, laptops have become thinner and all of their I/O ports have started disappearing. However, to solve this, along came dongles and docks.

USB-C docks like these are now seen all over offices, especially in “hot desk” environments, allowing an employee to sit down at any desk, plug in one cable, and immediately have a ready-to-use workstation. They’re also common in “coworking spaces”, where multiple companies and individuals share an office space.
However, I believe an old threat looms in this environment…
Review of USB Attacks#
We’ve all been told the same thing for years don’t plug untrusted USB devices into your computer.
Malicious USB devices can pose a large number of threats, such as:
🪲 Serving malicious files: Malicious USB storage devices may contain malicious files, such as unwanted .exe, tampered documents with exploits, etc.
👨💻 HID Emulation: So called “BadUSB”, “Rubber Ducky” or “Bash Bunny” devices may appear innocuous, but when plugged in they can emulate a keyboard and fire off hundreds of pre-programmed keystrokes per second. This can be used to steal data, install backdoors, or perform all sorts of other attacks.
⚡️ USB Killer: This one is a bit more extreme, but malicious USB devices may purposefully damage your computer by zapping the USB bus.
USB-C docks should be seen as no exception. In-fact, I believe they are a much bigger threat than traditional USB attacks, as people have learnt to trust name-brand USB docks, and don’t see them as a threat.
A Fun, Simple Proof-of-Concept#
To prove my point, I decided to create a simple, practical POC using a name brand USB-C dock with a hidden malicious implant.
Before we get to the horrors of my work, I’ll start with a demo:
So what’s happening here? Well, hidden inside the dock is a Raspberry Pi Zero W running P4wn P1 A.L.O.A - a brilliant framework for turning a Pi Zero into “A Little Offensive Appliance”. This can be used for a range of USB attacks, but here I’m specifically using it to inject keystorkes.
This can be abused to perform all sorts of attacks, such as:
- Stealing data.
- Installing a reverse shell.
- Performing malicious actions on the user’s behalf.
Installing the Implant#
It’s not *too* difficult to open these docks, but it takes some work. There is a rubber pad on the bottom stuck down with some adhesive, hiding a series of screws underneath. This makes it easy enough to disassemble, but quite tedious to open and examine. At a quick glance, it also looks unlikely someone could have opened it up and sealed it again.


Once disassembled, you can see there’s actually plenty of vertical space to hide malicious components.

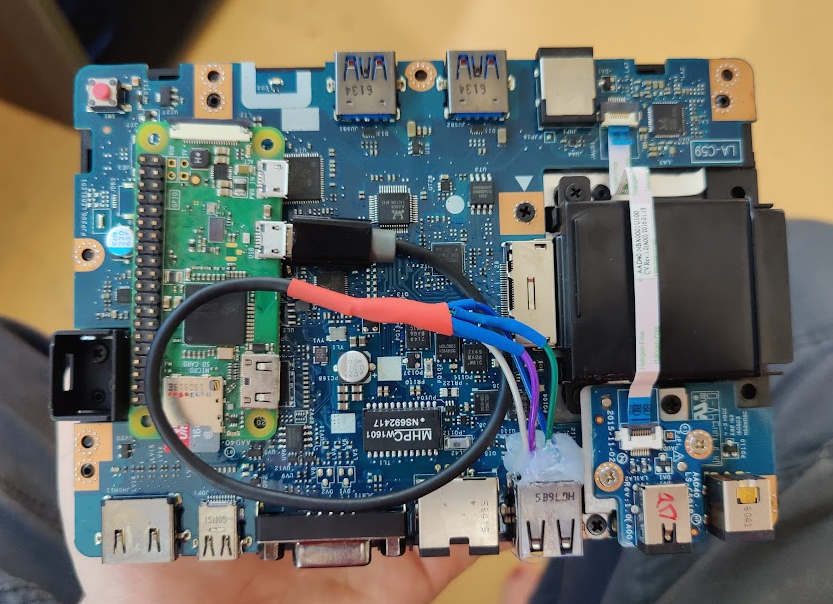
To keep things simple, I decided to just hijack one of the rear USB 2.0 ports by soldering some leads to the back of the connector.

This can then be simply soldered up to a micro USB cable connected to a Pi Zero.
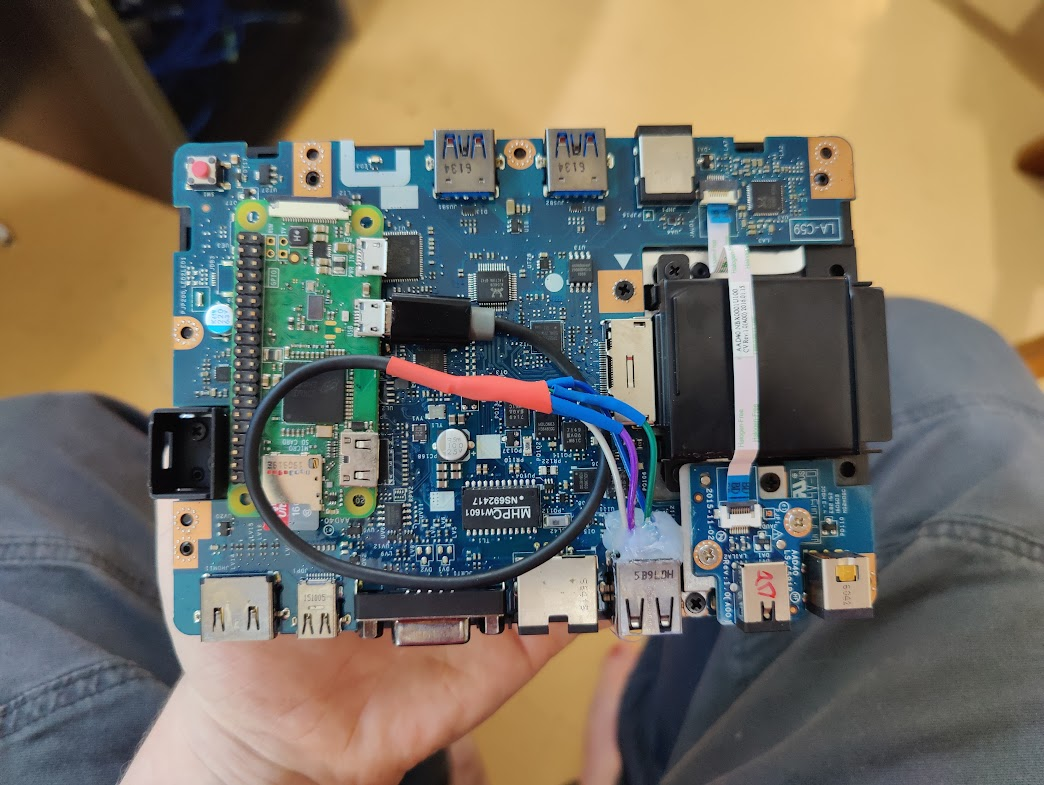
To prevent shorts, I also wrapped the Pi in electrical tape. To prevent the Pi from audibly rattling inside the case, I wrapped it several times until it was firmly in-place.

Can you tell the difference?#
Once re-assembled, it looks identical to the real thing:

It is not obvious the device has been opened, and the only notable side effects are:
- The top rear USB port doesn’t work anymore – this could be easily solved either by adding a small internal USB hub or wiring it via the Pi
- It is slightly heavier I guess?
Additionally, spoofing the USB vendor and product ID of the Pi allows it to appear genuine.
Realistically, you would have to open the device to determine whether or not it has been tampered with.
Conclusion & Further Ideas#
This fun little project took just a few hours from concept to POC, and clearly shows USB-C docks can be scary. Plugging in a malicious devices in a covert location certainly isn’t anything new, but there is a range of other attack surface here just waiting to be explored, such as:
Invisible key-logging: Inserting a malicious device in between a physical USB A port and the dock’s actual bus may allow an attacker to read everything you type, without you knowing. Very dangerous for stealing passwords.
Network tapping: Almost all USB-C docks have built-in ethernet ports. This offers a range of attack opportunities, from sniffing network traffic to acting as a persistent remote device.
Screen grabbing: Docks usually have HDMI ports, and whilst it would be difficult, it is very possible a malicious device could capture the user’s screen and send images/video back to the attacker. Inline HDMI capture devices already exist, and it wouldn’t be impossible to implant one into a dock like this.
I might explore some of these in future, but for now, keep being vigilant with what you plug in to your devices - especially in shared spaces.
Disclaimer#
The information in this article is provided for research and educational purposes only. Aura Information Security does not accept any liability in any form for any direct or indirect damages resulting from the use of or reliance on the information contained in this article.
