A Cost Effective Covert Implant for Red Teamers
Background#
During red team engagements, gaining initial access (a foothold within the network) is a critical objective. One effective method for achieving this is by using tools like the BadUSB, USB Rubber Ducky, or Bashbunny, which emulate Human Interface Devices (HID), such as a keyboard or mouse, and inject keystrokes to deliver predefined payloads. These tools allow an attacker with physical access to execute commands that can quickly backdoor a target machine. However, they do have limitations, including the requirement for the computer to be both unattended and unlocked.
To address these challenges, newer devices were developed which integrate WiFi for triggering payloads remotely. Some examples include the WiFi HID Injector, WiFi Duck, USBArmyKnife and P4wnP1, among others. These devices allow the red teamer to leave a malicious USB device plugged into a target machine, and deliver payloads from a distance (within WiFi range).
However, having an unfamiliar USB device plugged into your computer can raise suspicion, and unless the device is hidden, it is likely to be noticed by the target. This brings us to the concept of covert implants, which first came to light in the NSA’s ANT catalogue, specifically the COTTONMOUTH-I implant. The purpose of a covert implant is similar to the previous attack methods: delivering a malicious payload or acting as a key-logger. Unlike the previous devices discussed, these implants are designed to blend in as everyday items like USB cables, keyboards, or mice, making them much harder to detect.
Several devices have been released for red team use, including:
- O.MG Cables
- Created by MG, this device is in a league of its own and recreating it would take significant effort and skill. There is a wide range of variants covering all common USB connectors types / combinations and they are nearly indistinguishable from a normal charging cable.
Here is a quick pros and cons list (which is my opinion only):
| Component | Pro | Con |
|---|---|---|
| O.MG Cable | • Packed with features • Available in almost all USB variants • Actively developed | • Price - compared to the NSA COTTONMOUTH it is cheap, but if you need 20 of them and they get lost / broken by the customer (this happens), the price can quickly add up |
| Evil Crow Cable | • Price • Available in most common of USB variants • Actively developed | • Not as many features as the O.MG Cable |
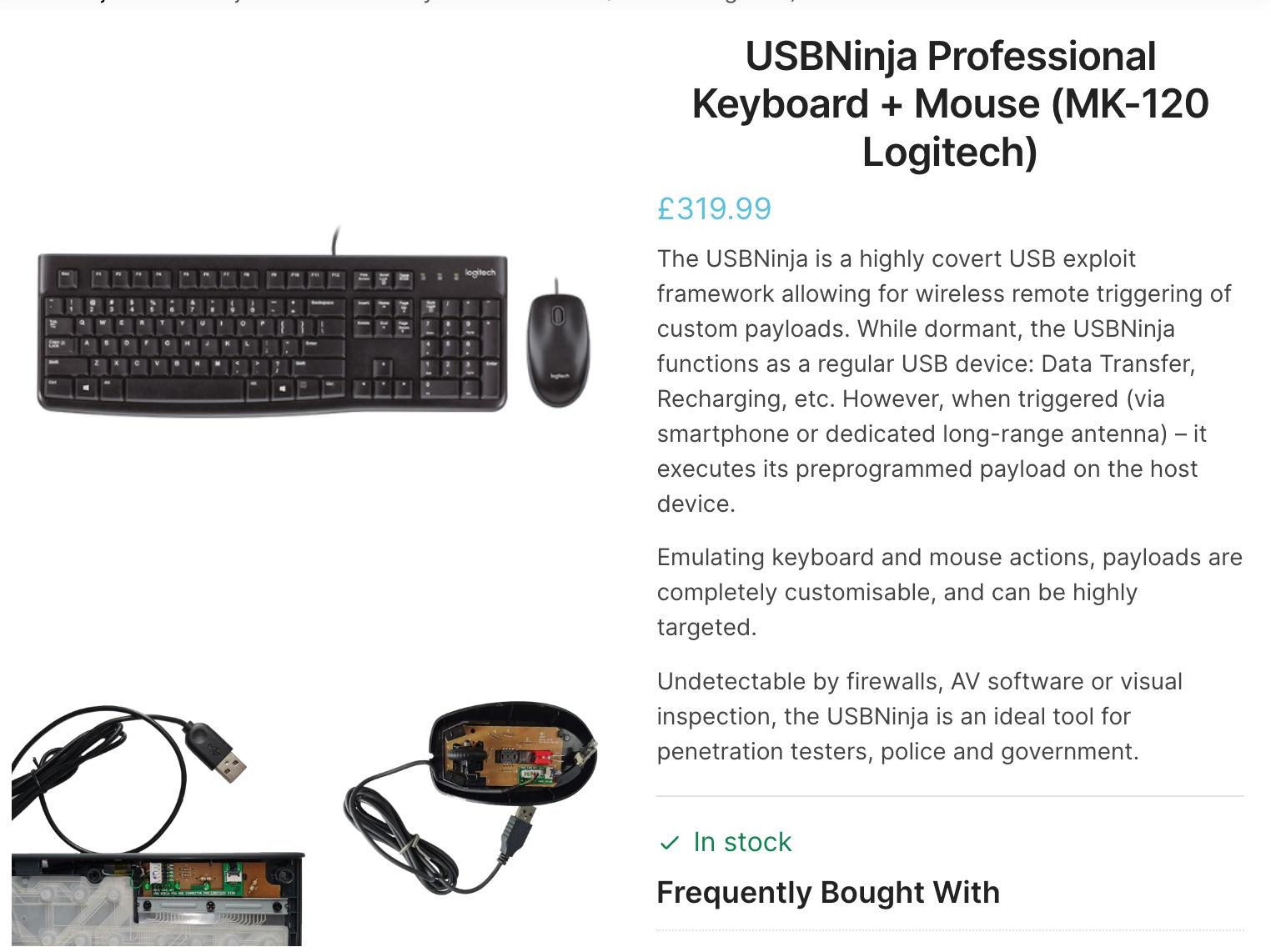
| USBNinja | • Available in almost all USB variants and directly inside a common keyboard / mouse | • Price • Does not appear to be under active development • Not as many features as the O.MG Cable |
If budget isn’t a factor for you / your organisation, then the O.MG cable is the clear “winner” and you likely won’t even need to consider building your own. The Evil Crow Cable would be my second choice considering the attractive price.
My aim is to create a low-cost implant that can be easily integrated into an existing peripheral, such as a wired keyboard or mouse. Installation is as simple as opening the peripheral’s case with a screwdriver and connecting the implant using the existing JST connectors. This approach requires no permanent modifications or soldering in the field. For added convenience, you could prebuild a few common keyboard or mouse variations with the implant already installed, which can then be swapped out even faster.
Wired mice may seem outdated and less common compared to wireless peripherals, but they are still being used. Funnily, I frequently encounter them in server rooms due to their simplicity and lack of reliance on drivers.
Keystroke Injection Delivery Methods#
Before diving in any further, it’s important to cover some common methods for delivering keystroke injection payloads through these implants. Note that this focuses on keystroke injection techniques, not keylogging or other features.
Auto-Run: This method automatically triggers the payload as soon as the implant is connected to the target device. However, it is only effective if the device is already unlocked and unattended and is not recommended for a covert implant that may be left plugged into an unattended target workstation or docking station overnight.
WiFi: The operator connects wirelessly to the implant, enabling them to send payloads remotely. However, this method requires the operator to visually confirm that the target machine is unlocked and unattended before triggering the payload.
Caps Lock Trigger: This method leverages the universal behaviour of the Caps Lock key, which toggles its state across all connected input devices. Here’s how it works:
- The operator inserts the implant into a locked device and turns on Caps Lock at the lock screen.
- When the user attempts to log in, their password will fail because it will be entered in uppercase due to the Caps Lock state.
- This prompts the user to disable Caps Lock and reattempt login.
- The implant monitors the Caps Lock state change and triggers the payload shortly after the user successfully logs in. While this method requires precise timing and isn’t foolproof, it can be effective when executed properly.
Implant Build Components#
USB Hub#
This build involves piggybacking on the existing wired mouse cable, so a USB hub is required to connect multiple devices through a single USB connection. I found a compact Adafruit CH334F Mini 2-Port USB Hub, which only costs AUD $6.49.
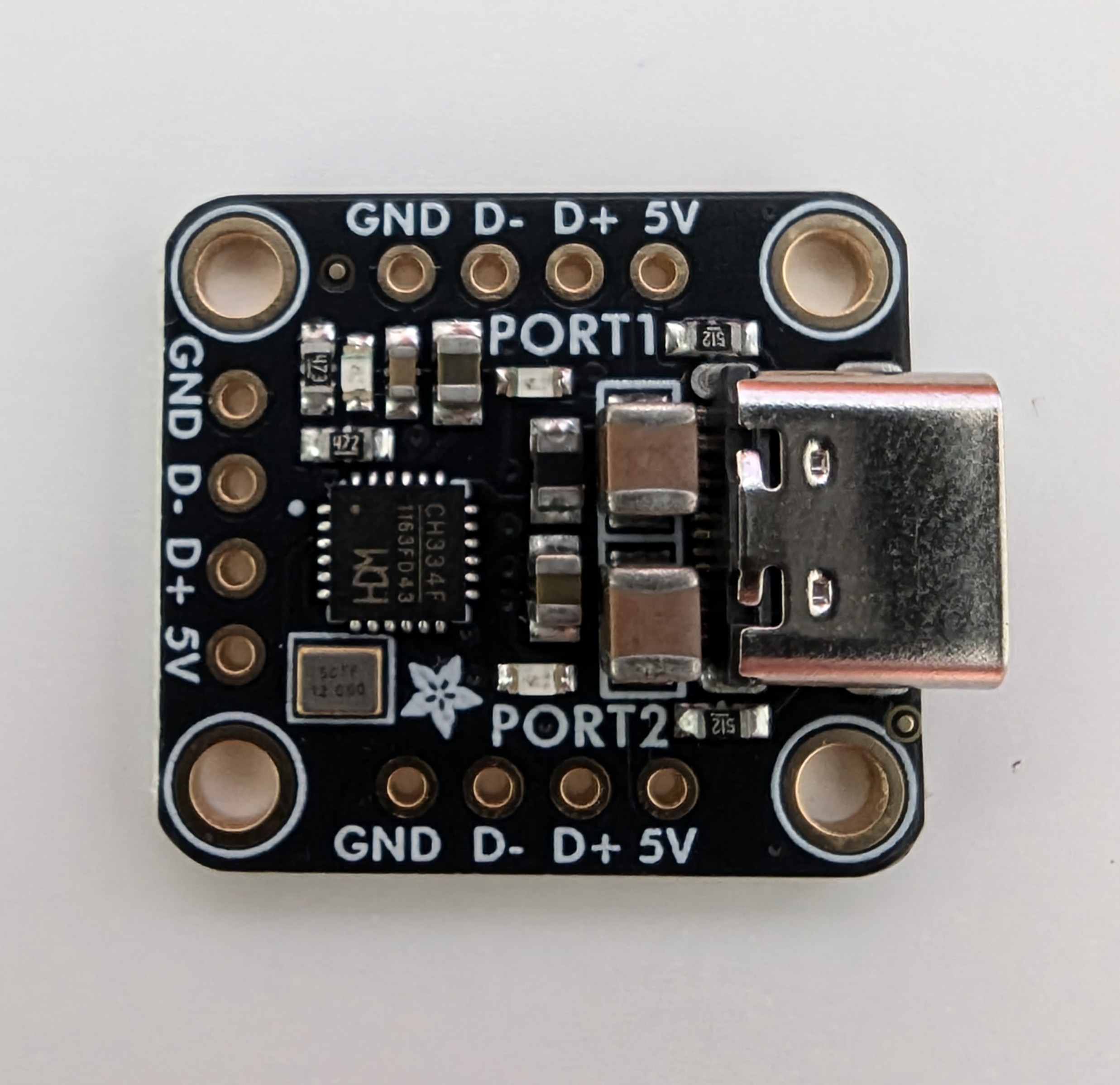
JST Connectors#
When dealing with keyboard and mouse internals, you’ll encounter a variety of connector types. Unfortunately, there’s no universal standard. These connectors are typically JST types with different pitches, such as 1.25mm, 1.5mm, or 2.0mm. To ensure flexibility in the field, you can prepare a few variations of connectors to accommodate the most common hardware you might encounter.
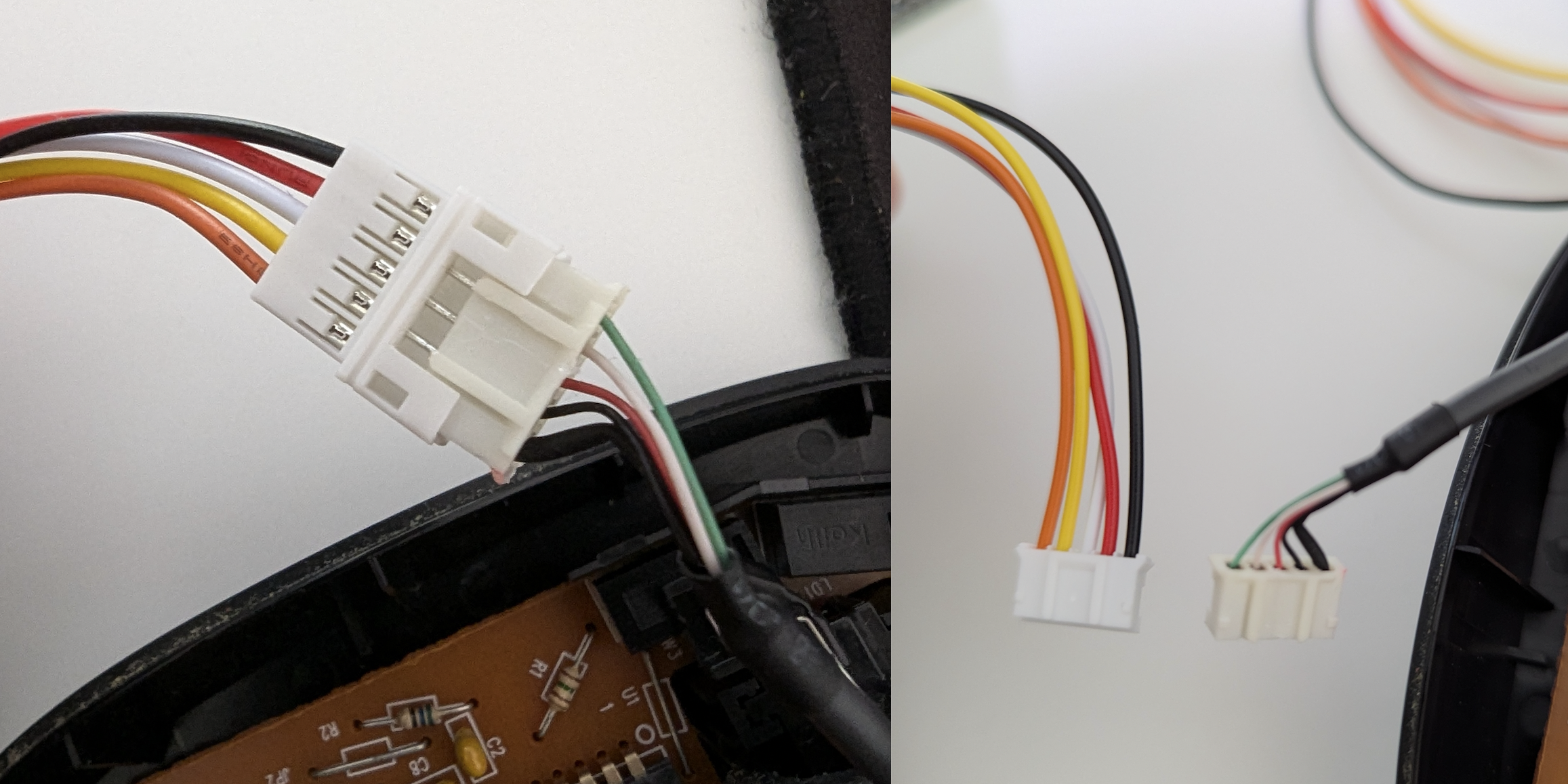
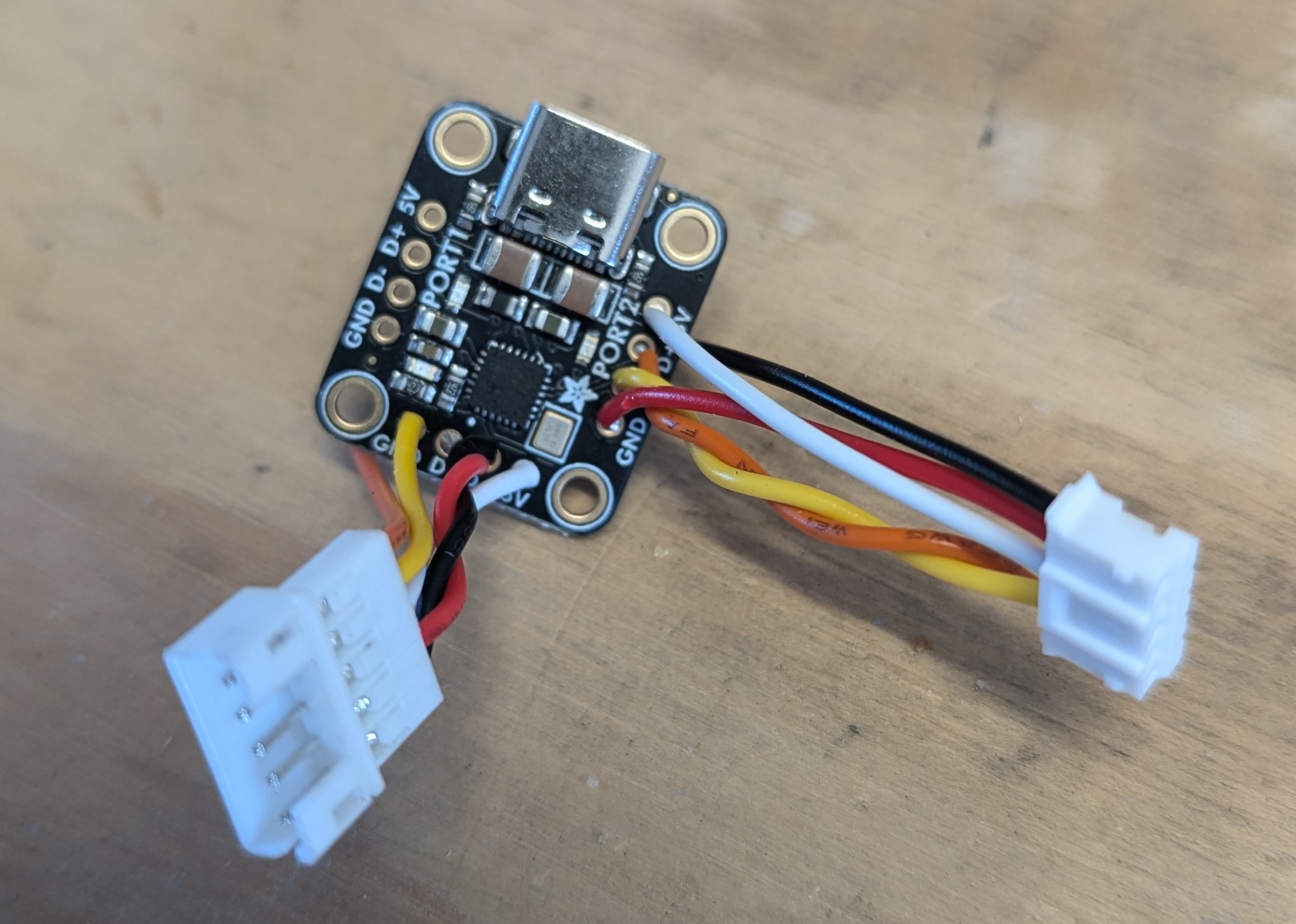
To create the mouse implant using the USB hub, I soldered two 5 pin JST 2.0mm connectors onto the hub. A male connector is attached to the upstream port of the hub, which connects to the mouse’s original USB cable. A female connector is soldered to the USB pins labelled Port 2, connecting back to the original port where the mouse’s USB cable was plugged in. This setup allows the hub to be installed in a wired mouse onsite during an engagement. A small microcontroller can be connected to Port 1 of the hub to serve as the malicious payload delivery system (i.e., badUSB).
JST connectors are really cheap, you can pick up a batch of 10 pre-soldered 5 pin JST PH 2.00mm connectors from AliExpress for around $3.00, or you can buy a crimp and connector kit to make your own.
Microcontrollers#
I’ve noticed that most of the equipment marketed for red teams tends to be overpriced. While I understand the need to account for R&D and development costs, the proliferation of powerful and affordable microcontrollers makes it difficult to justify the high prices some vendors charge. Without naming names, it’s hard to rationalise spending $50 (and this would be on the lower end of the scale) or more for something like a WiFi enabled Rubber Ducky when an ESP32 S3 zero can be purchased for as little as $7.
That said, the real value in these tools often lies in the software. Developing and maintaining firmware and software is a demanding, time-intensive process that requires significant expertise and passion. This deserves recognition, especially considering the level of support often expected by users. Without some form of financial incentive, it’s challenging to justify providing ongoing “Apple-level” support for these tools. However, for those willing to roll up their sleeves, there’s no shortage of cost-effective microcontrollers capable of serving as the foundation for BadUSBs or WiFi enabled Rubber Duckys.
So let’s take a look at some of the options of microcontrollers that are capable of emulating HID devices:
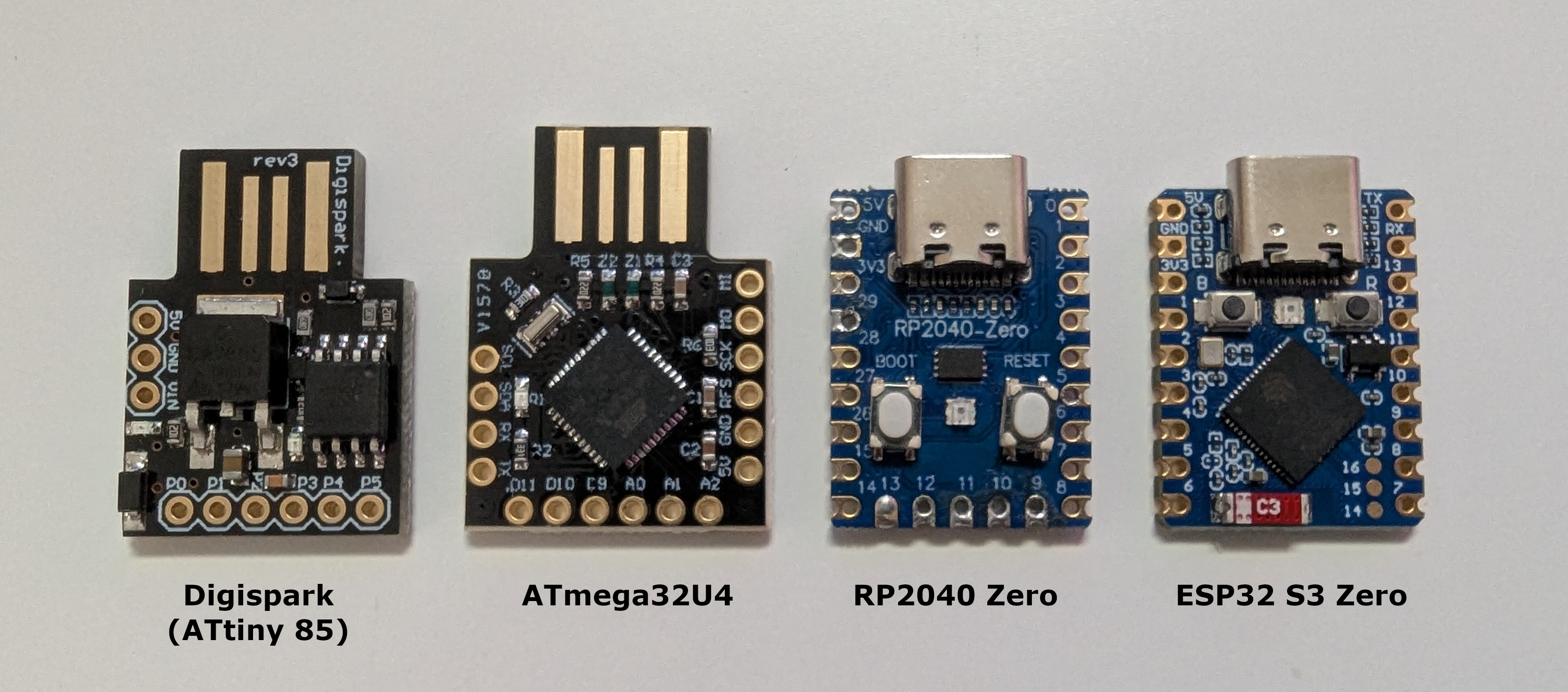
| Microcontroller | Cost (AUD) | WiFi |
|---|---|---|
| Digispark (ATtiny85) | ~ $5 | ❌ |
| ATmega32u4 | ~ $5 | ❌ |
| RP2040 Zero | ~ $6 | ✅ |
| ESP32 S3 Zero | ~ $7 | ✅ |
Note: You will also need a USB-C breakout board if you are planning on using any of the microcontrollers that have USB-C connectors. I bought a pack of 10 USB-C breakout boards for AUD $1.31.
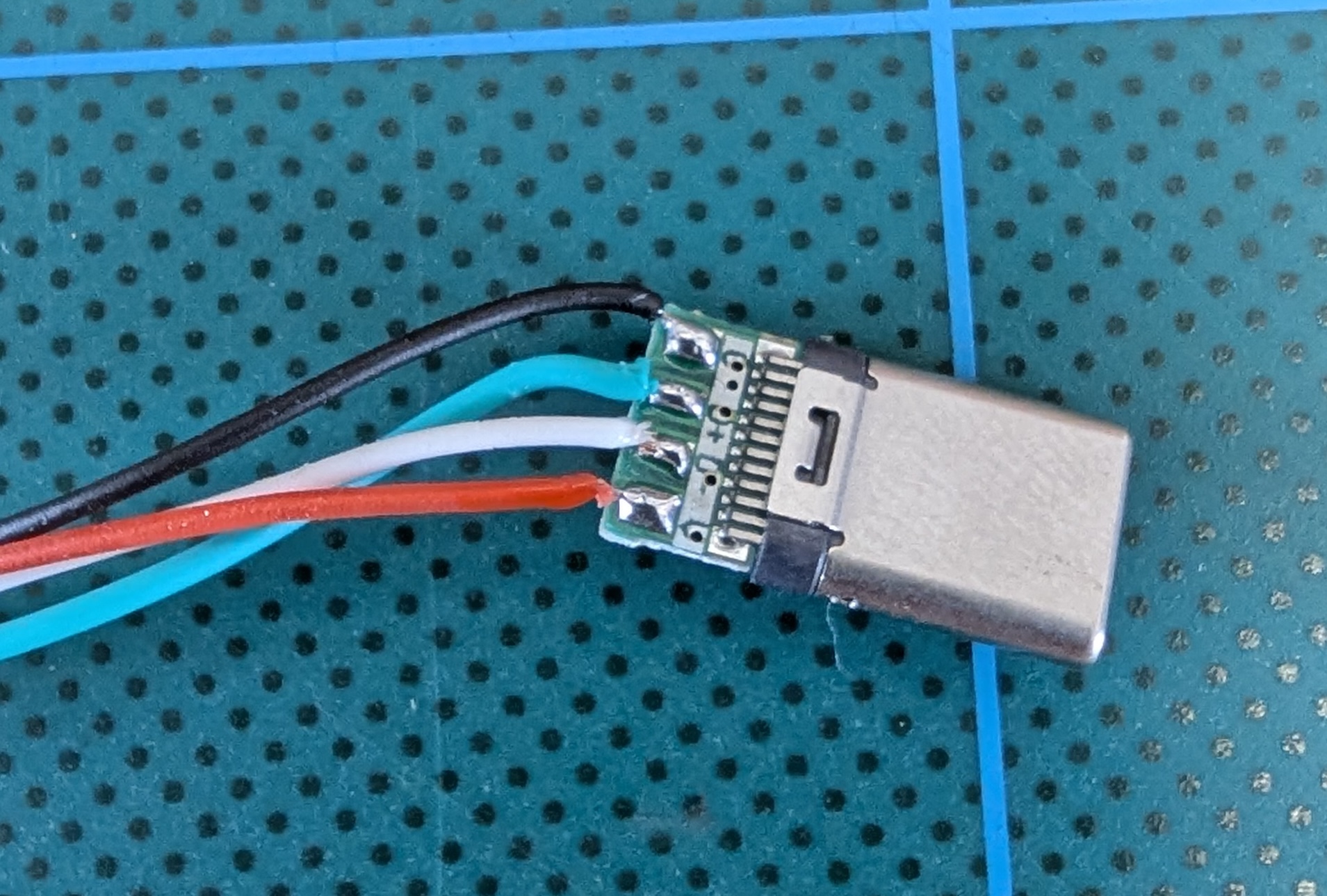
ESP32 S3 Zero Based Implant#
The smallest and most capable microcontroller that we can use to wirelessly deliver payloads via our mouse implant is the ESP32 S3 Zero.
We can use the SuperWiFiDuck project and make some small changes to the PlatformIO config:
Download default partition table: https://github.com/espressif/arduino-esp32/blob/master/tools/partitions/default.csv
Changes to PlatformIO config:
[env:esp32-s3-devkitc-1]
platform = espressif32
board = esp32-s3-devkitc-1
framework = arduino
monitor_speed = 115200
#for esp32-s3-zero
board_upload.flash_size = 4MB
board_build.partitions = default.csv
build_flags =
-DARDUINO_USB_CDC_ON_BOOT=1
-DBOARD_HAS_PSRAM
#upload_port = /dev/tty.usbmodem11101
lib_deps =
spacehuhn/SimpleCLI@^1.1.4
me-no-dev/AsyncTCP@^1.1.1
https://github.com/me-no-dev/ESPAsyncWebServer.git
-D USB_CUSTOM_DESCRIPTORS
-I custom_usb_descriptors
-D USB_PID=0x0002
-D USB_VID=0x303a
-D USB_MANUFACTURER='"Espressif Systems"'
lib_extra_dirs = custom_usb_descriptors
- Flash the ESP32 S3 Zero with the SuperWiFiDuck firmware using PlatformIO. You can do that using either the PlatformIO CLI or if you have some integration with your IDE.
Bill of Materials and Cost#
The component cost breakdown is estimated as below.
| Component | Price (AUD) |
|---|---|
| ESP32 S3 Zero | $6.65 |
| AdaFruit CH334F 2-PORT USB Hub | $6.49 |
| JST 2.0mm Pitch Male + Female Connector | $1.03 |
| USB-C Breakout | $0.13 |
| Total | $14.30 |
Note: The cost breakdown excludes the price of the mouse, as the implant is intended to be installed in an existing wired mouse or keyboard found in the field. However, if you prefer to prepare a few ready-to-deploy units, the Logitech MK-120 keyboard and mouse combo can be purchased for around AUD $25.
Demo#
Mouse Implant#
Caps Lock Trigger#
The code for this can be found here: https://gist.github.com/dunderhay/24a21e882d51befc0f8e2abcda075c11
Disclaimer#
The information in this article is provided for research and educational purposes only. Aura Information Security does not accept any liability in any form for any direct or indirect damages resulting from the use of or reliance on the information contained in this article.0
