
The Art of Persuasion: How Behavioural Science is Revolutionising Cybersecurity
Designing Security for the Human Experience - This article is part of a series.
The Context#
Let’s face it, changing human behaviour is hard and there are a lot of methods and theories out there. I’ve been studying some of them and reading about strategies on how to use different types of intervention strategies to change employee security behaviours, and their challenges, for quite a few years.
Security Awareness is a relatively new Cyber Security subdomain which is ever-changing and evolving, moving away from “security awareness” and into “human risk management” and shifting from compliance-only phishing campaigns to using behavioural science and psychology. Nobody has found a silver bullet strategy yet for influencing security behaviours. Managing human risk is A LOT more than just security awareness campaigns, as shown throughout this post.
Behavioural Science - The Missing Piece In The Security Awareness Puzzle#
The 2019 paper Acknowledging and Reducing the Knowing and Doing Gap in Employee Cybersecurity Compliance suggests that there are gaps between awareness (i.e. knowledge), intention and behaviour.
Traditional security awareness strategies mainly focus on awareness training information materials, e-learning videos, and phishing simulations. This increases knowledge (what) and people’s capability (how). However, similar to how facts don’t change our minds, knowledge doesn’t guarantee behaviour change either, although many security professionals think it does. That’s because one important aspect of behaviour change is MOTIVATION (why) - what people want to do and why they do it. You can feed your employees infinite amounts of knowledge, but if they don’t care enough about it to want to use it, it’s money and time thrown out the window. Enter behavioural science - the game-changing approach to managing Cyber Security human risk.
Disclaimer: I’m not a behavioural scientist, but I do have knowledge and plenty of ideas about this and I am stubborn enough to explore them. Here’s one of my ideas, with all the rationale and thinking behind it layed out below. I’m happy to have experts in the field scrutinise it, discuss it further and put it to practice if they see value in it.
Target Behaviours#
My three favourite Tier-1 security behaviours which every company and security awareness strategy is struggling to properly instil in their employees are:
- Use a password manager (to reinforce the behaviour of generating strong unique passwords)
- Use Multi-Factor Authentication (to add extra protection to credentials)
- Keep applications and systems up-to-date (to minimise vulnerabilities and exploits)
A Word of Caution#
Before we get too excited, it’s important to keep in mind that while these strategies can be an effective way to influence behaviour, it’s crucial to test their effectiveness, measure the results and adapt over time. Additionally, it’s important to make sure the behaviour intervention strategies are aligned with the users’ context and goals and to avoid creating any unintended consequences.
Chosen Tools#
Behaviour Change Models#
I chose two widely used and recognised behaviour change models - the COM-B Model and Fogg MAP (or MAT) Model. Both of them are explained and compared in detail in the The Behavioural Architects’ 2020 paper entitled Behavioural Change Models - An overview of the two best behavioural change models and how to apply them.
Both COM-B and Fogg MAP models can be applied to the task of designing an intervention strategy of encouraging people to do a set of target behaviours.
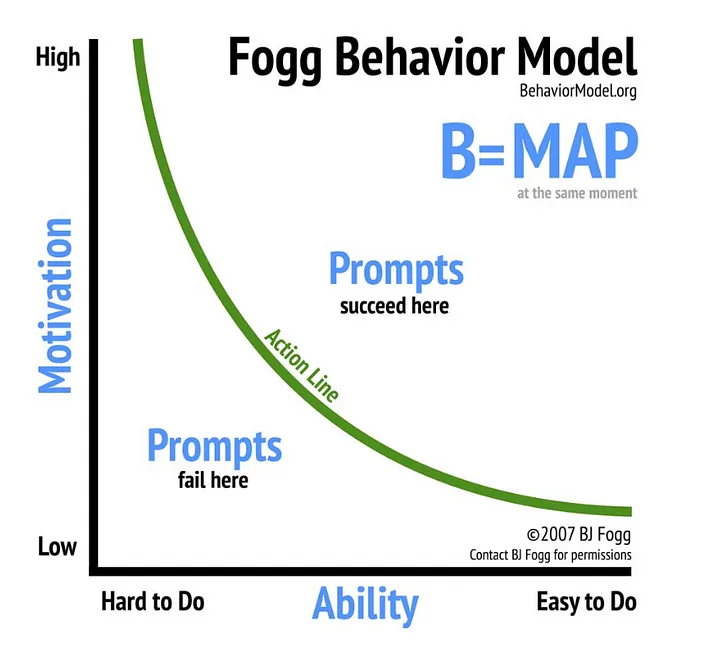
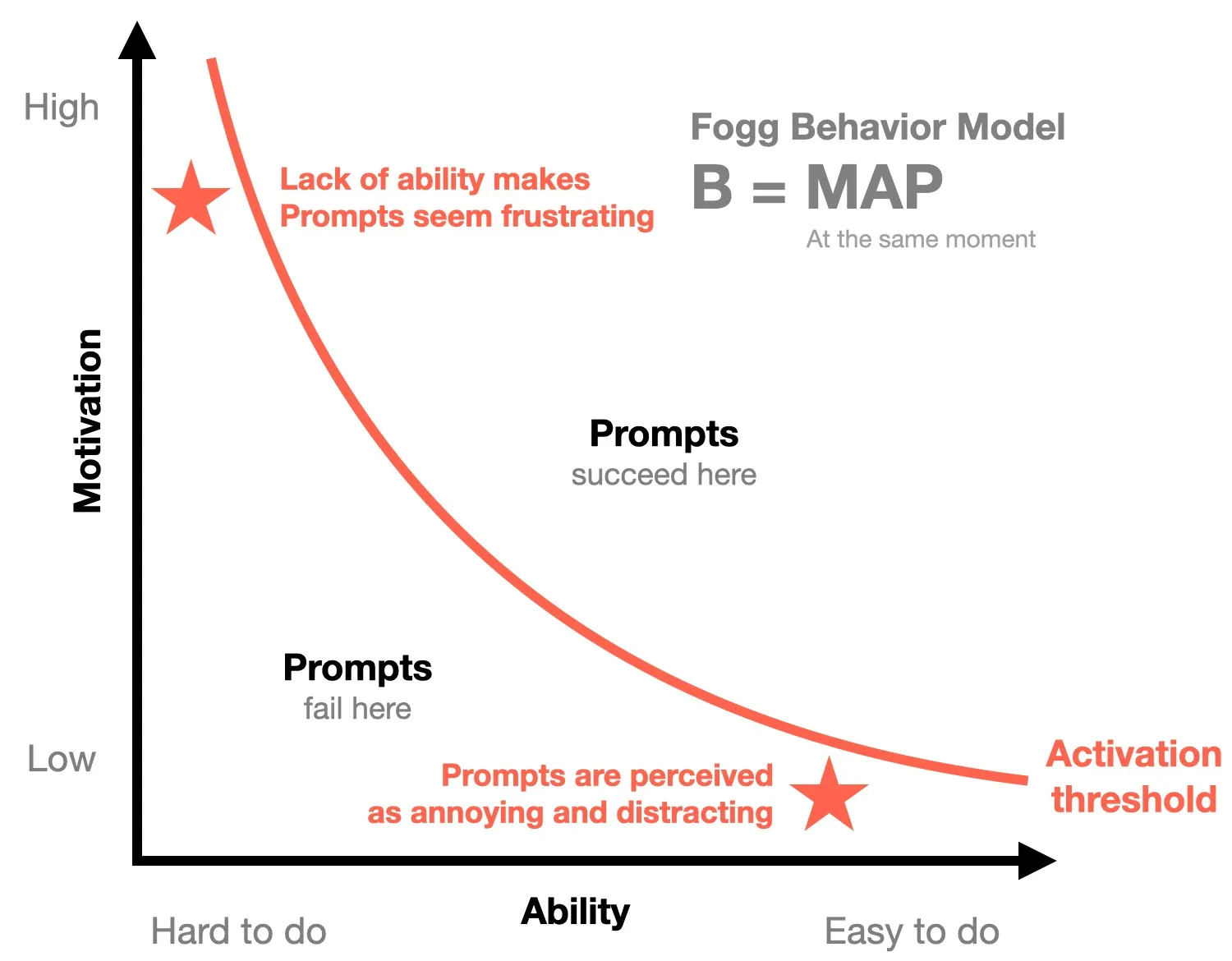
The Fogg MAP behaviour model, which stands for Motivation, Ability, and Prompts, is a framework for understanding how behaviour can be influenced.
Model strengths - Identifying how to trigger behaviour change. Specifically:
- In-context executional ideas, in the form of triggers, to steer people to adopt a target behaviour or stop an undesired behaviour.
- Problems or gaps in persuasion and influence to achieve a target behaviour or stop an undesired behaviour
The COM-B Model, which stands for Capability, Opportunity, and Motivation, is another useful framework for understanding the factors that contribute to a particular behaviour.
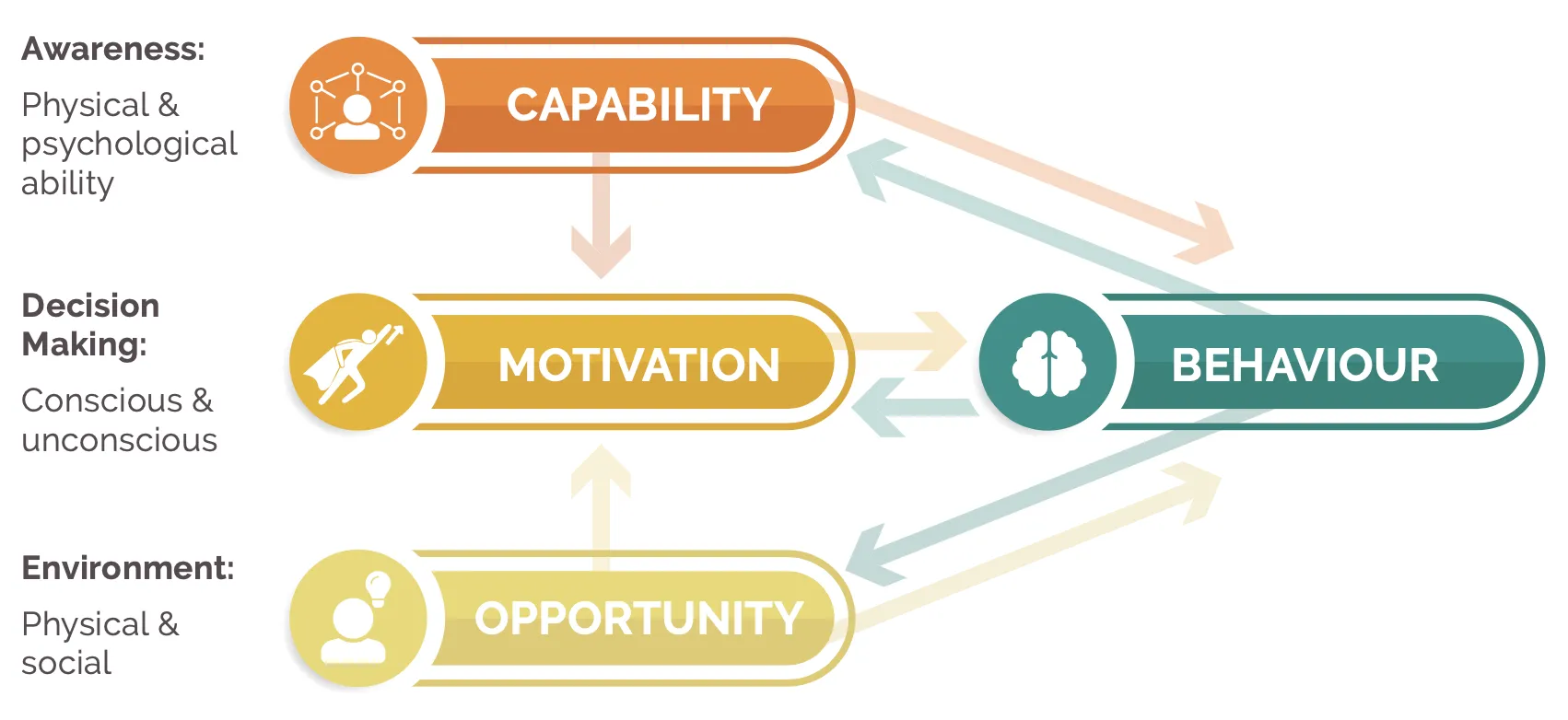
Model strengths: Like Fogg MAP, the COM-B model provides a structured analytical framework but is more focused on developing strategies around broader behaviour change challenges, often with complex multiple variables. For example, it might take the biggest barriers and identify how to build motivation or capabilities and skills from scratch, or how to provide increased opportunity, perhaps in the form of better facilities or technology.
Model Differences and Similarities#
According to The Behavioural Architects paper, both COM-B and Fogg MAP aim to a) understand behaviour and b) work out how to most effectively influence or change it to achieve a target behaviour and apply a systematic framework to thinking through behaviour change. The most notable differences in scope and aim between the models are:
- B=MAP is more suited to identifying incontext, instant solutions for persuasion using in the moment triggers, whereas COM-B is better suited to more strategic applications around broader behaviour change challenges, focused on filling in the gaps in people’s capability, opportunity and motivation.
- In the B=MAP model, motivation and ability are a trade-off and to some extent, a substitute for one another meaning that if someone has enough motivation and drive to do something, it might be enough to overcome any deficits in their ability and vice versa. The COM-B model however, assumes that motivation and ability (capability) are equally necessary and can also feed into each other, so if ability is raised, that might also boost motivation.
- In the COM-B model, triggers are incorporated within opportunity (physical and social cues or prompts) and are defined as just one of the three equally-weighted factors enabling a behaviour. In the B=MAT model however, triggers are seen as the ‘last mile’, the final element that might tip someone over the threshold to carrying out a behaviour and might involve only a small effort or in-context tweak to change.
- Types of motivation are more broadly defined in the COM-B model. The B=MAP model only really involves emotional (unconscious) types of motivation and does not consider reflective (conscious) types of motivation as COM-B does. In B=MAP, automatic (unconscious) habits are classed as a type of ability that can help facilitate a behaviour rather than an automatic type of motivation.
- B=MAP specifically incorporates the idea of scarce resources, such as money, time and mental bandwidth within the concept of ability, which isn’t specifically included in the COM-B model and could be considered a weakness. All three of these factors could likely be significant enough barriers to doing a desired behaviour, yet someone applying the COM-B model might not specifically be prompted to consider them.
Which one to choose? To summarise the above, the Fogg MAP model can be used for situations dependant on context (e.g. flossing when you brush your teeth) which need a ‘last-mile’ prompt to trigger the desired behaviour - this can be used to make or break habits. The COM-B model can be used to design a long-term behaviour change strategy focused on filling in crucial gaps in people’s capability, opportunity and motivation.
For this reason, the behaviour change model of choice in cyber security seems to be COM-B, and it’s the one I chose as well. However, the Fogg MAP model can also be used for in-context situations like employee on-boarding. So there can be 2 entirely different security behaviour change design strategies - one used during employee on-boarding and one for overall long-term employee behaviour change.
Nudge Theory#
Nudge theory is a concept in behavioural science that suggests that small, subtle changes to the environment or decision-making process can influence behaviour in a desired direction without forcing or prohibiting a particular action.
A very good explanation and primer on nudges can be found here. I wrote about the implications and challenges of using nudges to influence security behaviour before.
Common types of nudges include setting a default option (i.e. the option that an individual automatically receives if they do nothing), creating a psychological anchor, changing the ease of choosing certain options, changing the salience of certain options, informing people of something, reminding people of information they already know, reminding people to do something, and getting people to slow down.
Nudges are an effective solution due to their capacity to alter decision-making outcomes predictably. For example people are more likely to choose a particular option if it is the default option.
The Fogg MAP and COM-B can use nudges to trigger someone to do the behaviour, particularly if they have almost enough motivation and ability/capability and just need a final push.
ChatGPT#
I already used ChatGPT in anger for the past few months to understand how to influence its generated results. I was inspired to use ChatGPT for this topic after I read a recent post by behaviour science expert Samuel Salzer. By the way, if you want to use ChatGPT as a power user, this LinkedIn post has some great resources.
For the initial prompt I asked ChatGPT to generate the initial COM-B and Fogg MAP statements, and a list of nudges - “I want you to act as a behavioural science advisor. I will provide you with a target segment and target behaviour, and your task is to help with a detailed behavioural mapping using the three factors of the COM-B Model and BJ Fogg’s MAP behaviour model. In addition, you should use your knowledge of behavioural science and psychology to create an effective step-by-step intervention strategy that a company can follow in order to achieve positive results. My first request is: “Help me design an intervention strategy to get employees (target segment) to do three target behaviours: 1 - Use a password manager, 2 - Use multifactor authentication, and 3 - keep their applications and systems they use updated”.
Then I tweaked the results in subsequent prompts and asking ChatGPT to mix and match them:
- Every user’s motivation is slightly different, but most user’s motivation will be to get their jobs done with as little interruption as possible from the security actions they are being asked to perform. Integrate this into your suggestions and rewrite your initially suggested COM-B and Fogg MAP intervention strategies.
- For each target behaviour and suggestion you made, use nudge theory to reduce user friction in performing the desired action or behaviour.
- Integrate each of these nudges into the COM-B and MAP statements you generated. Here’s an example of what ChatGPT’s results look like:
The generated results weren’t perfect, I still had to filter out and modify inaccuracies.
By the way, if you know what you want from ChatGPT (i.e. give it the right input) and have the patience to ask it to modify the generated results until you get to a close-enough version of the content you’re after, this AI chatbot can save you time. It’s quite an enjoyable process too, you’re basically an AI orchestra conductor.
Assumptions for Designing the Security Behaviour Change Strategy#
Before designing the behaviour change intervention strategy, I’ve made some initial assumptions as follows.
Assumption 1 - choosing which behaviour change variables to control#
Both COM-B and Fogg MAP behaviour change models have roughly the same components - Motivation, Ability/Capability, and Prompt (or Trigger)/Opportunity (in COM-B triggers are incorporated within opportunity). We will focus solely on those component variables that are within our control.
Assumption 2 - controlling the Motivation variables#
- Reflective thought motivation (from the COM-B model) is where employees reflect on whether to do a behaviour through analytical and conscious thought, considering their goals, plans, beliefs and identity in weighing up whether to go ahead.
- Every employee is different, especially regarding their beliefs and identity. This is undeniably something extremely hard to control using behaviour change strategies, and even if it would be successful for a group of people, it would fail for others.
- Most people don’t care about cyber security in their day-to-day life (sorry folks, but it’s the truth).
- It’s widely known that security works best when it doesn’t impact business or productivity.
- Using all of the above to simplify the proposed strategy, I assumed that most people’s reflective thought motivation will be to complete their day-to-day tasks with as little interruption as possible, including interruptions from the security actions they are being asked to perform (like using MFA, or updating their software).
- Anticipation (from the Fogg MAP model) can be used for behaviours motivated by fear or hope. Since we’re dealing with people not animals, and I’m a fan of the carrot and not the stick (positive reinforcement works best), I will use hope generated anticipation using rewards in designing the strategy. This way the employee has something to hope for - the reward, rather than something to be afraid of - e.g. repercussions from not doing the security behaviour they’re asked (think naming, blaming, shaming, which are proven to be ineffective and toxic).
- Note: we can use rewards to increase motivation in the short term, such as for increasing the chances of a behaviour to become a habit. Thanks to hedonic adaptation I wouldn’t rely heavily on it beyond long-term though, and also because each individual’s intrinsic motivation can be more powerful than artificially created ones through external rewards. It’s the same reason why giving employees more money instead of feeding what truly motivates them doesn’t mean they will be happy with their job.
- Belonging (from the Fogg MAP model) - i.e. gain acceptance by our peers and avoid rejection.
- Because this can fluctuate during an employee’s day-to-day life, I propose using this motivation when it’s at its peak - when joining a new company, more specifically during the on-boarding period. I assumed that if someone decided to join a new company, they also want to make a good impression (at least in most cases) in the first few weeks by following the rules and staying out of trouble (like not causing a ransomware incident in their first week) to show that they belong in the new workplace.
- Belonging motivation can also be used outside of on-boarding, especially in cases where the company culture is promoting cyber security behaviours. An employee expressing such behaviours shows that they belong in that culture.
Assumption 3 - controlling the Capability/Ability variable#
Whether an individual has the necessary skills and mental ability to do the desired behaviour. This is where I want to concentrate efforts, and what can either make or break the strategy. The proposed strategy makes the following assumptions:
- Time (from the Fogg MAP model)- time is a scarce resource for any employee so I want to minimise the time it takes to perform the target behaviour
- Habit/routine (from the Fogg MAP model) - it’s safe to assume that the target security behaviour is not part of the employee’s habits; I do want to design the strategy so that it has a good chance of becoming part of their habit or routine - this can be encouraged short-term through rewards as mentioned in Assumption 2
- Psychological capability (from the COM-B model)- this includes
- knowledge - increasing employee knowledge (i.e. using training) and support on how to perform the target behaviour as early as possible (e.g. after they just downloaded the password manager and started using it for the first time) should yield the best chances of the security actions becoming mentally “easier” to perform with each repetition
- cognitive or mental capability (how much do employees need to think when performing the target behaviour - i.e. how hard is it to do?) - we need to assume that employees have limited mental bandwidth to perform extra tasks outside their day-to-day ones so again I want to minimise the mental effort required to perform the target behaviour; this can be achieved using the same techniques used to increase knowledge
- ability to self-regulate (i.e. control one’s behaviour and actions if needed)- self-regulation depends on too many physiological and psychological factors that vary throughout a day, so we have to assume that not everyone will be equally able to self-regulate at any given time and some employees will lack the patience to download and learn how to use the proposed security tools; again making things as easy as possible for them is key
To sum up Assumption #3, I want to:
- Minimise the time it takes to start the target behaviour (e.g. download a tool, configure it, use it) so that that interruptions are cut short
- Provide as much knowledge, training and support to the employees so that they are well equipped in knowing what to do when they perform the target behaviour, thus reducing mental effort and interruption time
- The two items above can be supported by facilitator type Prompts/Triggers (see Assumption #4) which would either simplify the task (make it easier) or increase the employees ability/capability to perform the security behaviour (through quick tips for example)
In other words, we want to make it as easy as possible for the security behaviour to be expressed by the employee, and reduce friction to the minimum.
Assumption 4 - choosing Prompts/Triggers#
To create Opportunity factors that lie beyond the individual that might help enable a behaviour, or make a behaviour possible or prompt it, for example prompts in the surrounding environment.
- culture - I can’t emphasise enough how critical it is to have a strong security-focused culture on top of a positive and psychologically safe workplace culture; more on this in a dedicated section below
- space, time and physical device - the security behaviours can be prompted based on space (e.g. when in the office, or remote) or time (e.g. when someone wants to log-off or shutdown their computer) or even physical device - when someone is on their smartphone, tablet, or laptop.
- social opportunity - we want to capitalise on this and show that the target security behaviour is performed by others, further encouraging the employee to also perform this behaviour - Cialdini’s social proof nudges can be useful here. Also having designated security champions provides the employees with cyber security role models from their in-group to influence and support them.
- just in time prompts - the prompt or triggers needs to happen at the right time.
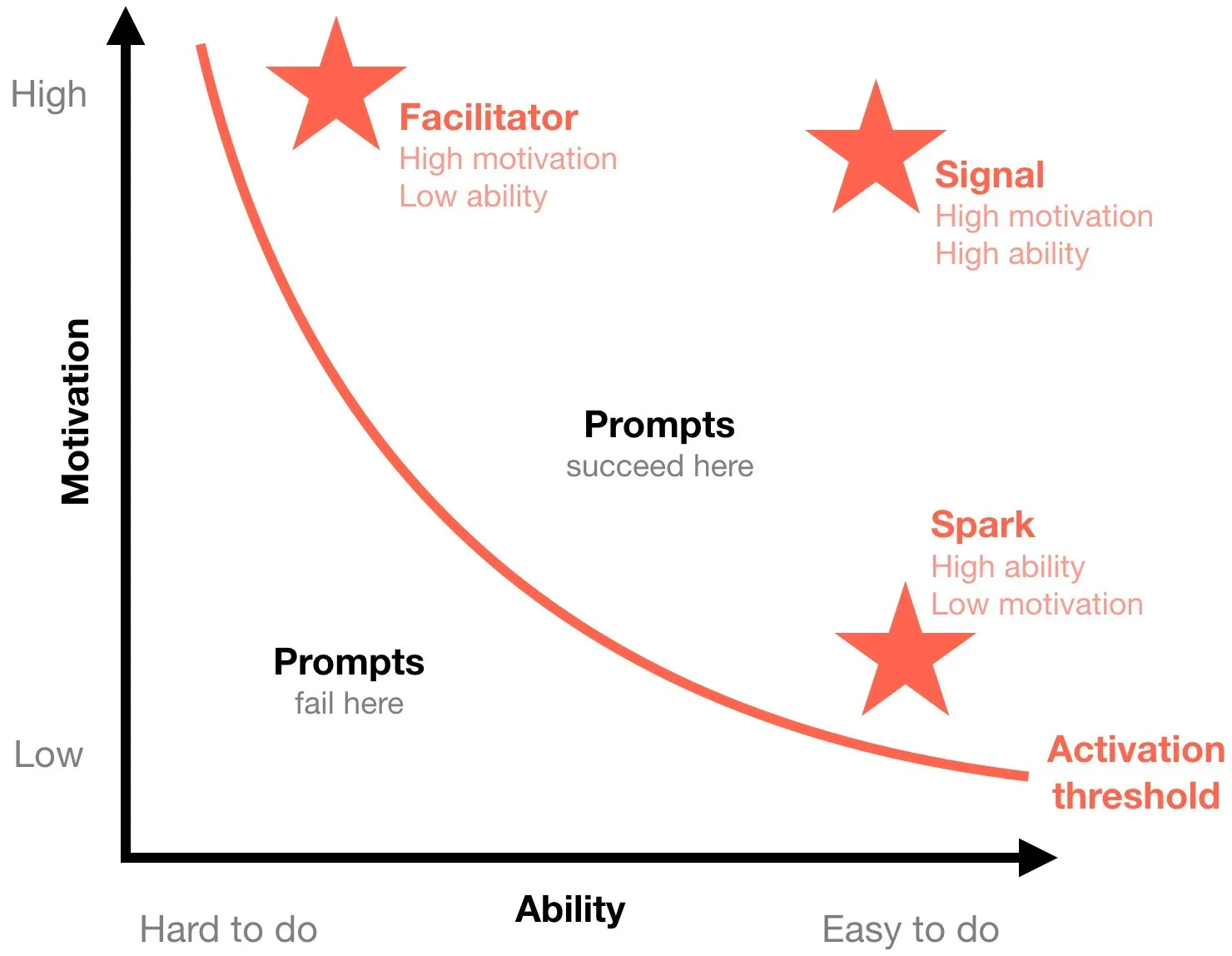
- If a person is placed below the activation threshold (insufficient motivation and ability to perform a behaviour in the first place), then a prompt might not lead to the target behaviour. Instead, the prompts become frustrating, annoying or distracting (think of ads, pop-ups, spam emails).
- An example of a well-timed everyday facilitator prompt or cue can be in the form of a baloon tip when you need something while using an app (remember Clippy, Microsoft’s helpful paperclip assistant?).
- A new employee on-boarding period can be a great spark prompt, using the fresh start effect (where goals are more likely to be achieved at the start of a new period), coupled with the motivation of belonging in the new workplace. On-boarding periods are also backed up by many facilitator prompts because the new employee will be undergoing training and inductions, and receive technical support.
- The most common everyday signal prompts are reminders (emails, pop-ups, etc). This can be used for the long-term behaviour change intervention design strategy rather than during on-boarding.
- nudge ethical principles - I used a good list of basic principles from Effectiviology
- Nudges shouldn’t necessarily be hidden
- People should perceive the nudge as beneficial
- People should feel that the nudge respects their ability to choose
- People generally prefer nudges that target their conscious reasoning
The Security Behaviour Intervention Strategy#
As mentioned in the previous sections, I propose using the Fogg MAP model as the short-term strategy during an employee’s on-boarding period because their motivation to comply, fit in and “do well” during the first weeks after starting a new job is high. The MAP model will thus be used to create new security habits for the employees, and the COM-B model (used as the long-term behaviour change strategy) will aim to provide the best chance for the newly formed habits to “stick”. Since the COM-B model is suitable for strategic applications around broader behaviour change challenges it also serves as the basis for the behaviour change intervention strategy for existing employees.
Note: Some of the Fogg MAP and COM-B statements and nudges will be used for both strategies presented below. This is by design, as many apply to both scenarios (short and long-term).
Short-term Behaviour Change Intervention Strategy using Fogg MAP Model during Employee On-Boarding#
1. Use a password manager#
- Motivation:
- Show the employees the benefits of using a password manager, such as improved security and how it can make their job easier and more productive by reducing the time and effort required to remember and type credentials.
- Create a gamified system where employees can earn rewards for using the password manager, such as access to premium features or recognition within the company.
- Use a reward system, where employees are rewarded with bonuses or other incentives for reaching certain milestones in securing their accounts, such as securing a certain percentage of their accounts or not having any duplicate passwords.
- Nudges:
- Highlight the security risks of not using a password manager and how it can protect employees from them.
- Show a progress bar or similar visual representation when users are creating accounts or changing their passwords, to give them a sense of accomplishment while they use the password manager.
- Sharing testimonials (social proof) from other employees within the company who have found the password manager to be useful and convenient.
- Ability:
- Provide training and resources to make it easy for employees to set up and use a password manager for the first time, with minimal interruption to their workflow.
- Include the option to use the password manager as part of the company’s onboarding process for new employees.
- During the on-boarding process assign a security champion from the new employee’s team, who can assist them with any questions or queries.
- Nudges:
- Offer one-on-one training sessions for employees to set up and use the password manager.
- Set and push a default password manager application on the employee’s devices as part of the on-boarding process for new accounts.
- Prompts:
- Encourage employees to use a password manager by setting a reminder and positioning it as part of their productivity tools.
- Throughout their on-boarding period show a notification or pop-up message reminding employees to use the password manager when they log into a new account or change a password.
- Throughout their on-boarding period show a pop-up message on login screens of different tools and apps that employees are using and remind them to use password manager.
- Throughout their on-boarding period send regular reminders to employees about the importance of using a password manager, and the benefits it provides.
2. Use Multi-Factor Authentication#
- Motivation:
- Show the employees the benefits of using multi-factor authentication, such as improved security.
- Nudges:
- Highlight the security risks of not using multi-factor authentication and how it can protect employees from them.
- Share testimonials (social proof) from other employees within the company who have found the password manager to be useful and convenient.
- Ability:
- Provide training and resources to make it easy for employees to set up and use multi-factor authentication for the first time, with minimal interruption to their workflow.
- Include the option to set up multi-factor authentication as part of the company’s onboarding process for new employees.
- During the on-boarding process assign a security champion from the new employee’s team who can assist them with any questions or queries.
- Nudges:
- Offer one-on-one training sessions for employees to set up and use multi-factor authentication.
- Use the “opt-out” method, that is, setting multi-factor authentication as the default option for systems they use, making it easier for employees to use it without having to actively choose it.
- Set and push a default multi-factor authentication application on the employee’s devices as part of the on-boarding process for new accounts.
- Prompts:
- Encourage employees to use multi-factor authentication by setting reminders and showing the benefits of doing it.
- Throughout their on-boarding period send regular reminders to employees about the importance of using a multi-factor authentication, and the benefits it provides.
- Throughout their on-boarding period show a pop-up message on login screens of different tools and apps that employees are using, and remind them to use multi-factor authentication.
3. Keep applications and systems up-to-date#
- Motivation:
- Show the employees the benefits of keeping their applications and systems up to date, such as improved security and performance.
- Nudges:
- Highlight the security risks of not keeping their applications and systems up to date and how it can protect employees from them.
- Show the employees the number of security vulnerabilities that have been fixed by updates in the past, or incidents avoided.
- Ability:
- Provide training and resources to make it easy for employees to check for and install updates.
- Include the option to set up automatic updates as part of the company’s onboarding process for new employees.
- Offer one-on-one training sessions for employees on how to check for and install updates.
- During the on-boarding process assign a security champion from the new employee’s team who can assist them with any questions or queries.
- Nudges:
- Show a progress bar or similar visual representation of the progress made on updating the systems and apps, to give employees a sense of accomplishment.
- Set up automatic updates on the employee’s devices as the default option, as part of the on-boarding process for new accounts.
- Prompts:
- Encourage employees to keep their applications and systems up to date by setting reminders and automating update features on the systems they use.
- Send notifications when updates are available and remind employees to install the updates.
- Throughout their on-boarding period send regular reminders to employees about the importance of keeping their applications and systems up to date, and the benefits it provides.
- Throughout their on-boarding period set reminders for employees on a regular basis, to check for updates on their devices and applications and show them their progress on updating them.
Long-term Behaviour Change Intervention Strategy using COM-B Model#
1. Use a password manager#
- Capability: employees need to have the necessary technical knowledge to set up and use a password manager. This could include understanding what a password manager is, how it works, and how to install and configure it on their device. Minimise time and effort by:
- Providing simple and clear instructions and a user-friendly interface for setting up and using a password manager, with minimal requirements
- Providing a mobile app version of the password manager that employees can use on the go, to increase capability.
- Giving employees the option to call for help for technical support if needed with a 1-click option.
- Assigning security champions within the employee’s team to help them with any issues when configuring or using the app.
- Nudges:
- Providing a default option that pre-selects the use of a password manager or setting a default password manager for new accounts.
- Opportunity: employees must have easy access to a password manager. The company can provide easy access to an approved password manager tool. Increase opportunities by:
- Ensuring that downloading the password manager is possible and easily accessible to the employees from anywhere (remote or office) and on any device (smartphone, laptop, tablet). This can be achieved by making the password manager available to employees on all devices they use for work.
- Assigning security champions within the employee’s team to set a good example of using the app.
- Nudges:
- Use social proof, to show employees that others in the company are using password managers, and remind them of the benefits of doing so. - Highlight the option to use a password manager on all login screens and make it more prominent.
- Enabling helpful tips within the app, if available.
- Motivation: employees need to see the value in using a password manager, such as improved security and convenience. The company can communicate this value proposition and the risks of not using one. Increase motivation by:
- Showing the employees how the password manager can help them to be more productive, by providing a secure and convenient way to manage their passwords, and by reducing the time and effort required to remember and type credentials.
- Creating a gamified system where employees can earn rewards for using the password manager, such as access to premium features or recognition within the company.
- Using a reward system, where employees are rewarded with bonuses or other incentives for reaching certain milestones in securing their accounts, such as securing a certain percentage of their accounts or not having any duplicate passwords.
- Showing a progress bar or similar visual representation when users are creating accounts or changing their passwords, to give them a sense of accomplishment, while they use the password manager.
- Nudges:
- Sharing testimonials (social proof) from other employees within the company who have found the password manager to be useful and convenient.
- Using a referral, by having the employees invite their colleagues to use the password manager, and rewarding the employee who gets the most colleagues to use the password manager.
2. Use Multi-Factor Authentication#
- Capability: employees need to understand what multi-factor authentication is, how it works, and how to set it up on their devices and accounts. Minimise time and effort by:
- Providing simple and clear instructions and a user-friendly interface for setting up and using multi-factor authentication, with minimal requirements.
- Giving employees the option to call for help for technical support if needed with a 1-click option.
- Assigning security champions within the employee’s team to help them with any issues when configuring or using the app.
- Nudges:
- Using the “opt-out” method, that is, setting multi-factor authentication as the default option for systems they use, making it easier for employees to use it without having to actively choose it.
- Providing different options for multi-factor authentication such as push notifications, and biometrics.
- Using a referral, by having the employees invite their colleagues to use multi-factor authentication, and rewarding the employee who gets the most colleagues to use it.
- Opportunity: employees must have access to systems or applications that support multi-factor authentication. The company can identify and provide access to these systems. Increase opportunities by:
- Making multi-factor authentication available and easily accessible to the employees. This can be achieved by providing a single sign-on for all the systems, applications and tools the employee is using.
- Assigning security champions within the employee’s team to set a good example of using the app.
- Nudges:
- Using social proof, such as displaying the number of employees who are currently using multi-factor authentication, to encourage others to do the same.
- Motivation: employees need to see the value in using multi-factor authentication, such as improved security. The company can communicate this value proposition and the risks of not using it. Increase motivation by:
- Showing the employee how multi-factor authentication can help them to be safer online, by providing a secure way to access their work tools and applications.
- Creating a competition where employees who set up multi-factor authentication are entered into a drawing for prizes.
- Using a progress bar or similar visual representation to show employees how many of their accounts are protected by multi-factor authentication, and how much progress they have made in securing all their accounts.
- Nudges:
- Sharing success stories (social proof) of other companies that have improved their security by implementing multi-factor authentication.
3. Keep applications and systems up-to-date#
- Capability: employees need to understand the importance of keeping their applications and systems up to date, as well as how to check for and install updates. Minimise time and effort by:
- Making updating their applications and systems as easy and seamless as possible by providing clear instructions and automated updating features.
- Giving employees the option to call for help for technical support if needed with a 1-click option.
- Assigning security champions within the employee’s team to help them with any issues.
- Nudges:
- Using defaults and pre-selections, so that the default option is to update the systems when a new update is available.
- Opportunity: employees must have access to applications and systems that can be easily updated, and be aware of the update feature. Increase opportunities by:
- Making updating easy by providing access to systems that can be updated automatically.
- Assigning security champions within the employee’s team to set a good example of keeping apps up-to-date.
- Nudges:
- Using social proof, to show employees that others in the company are keeping their applications and systems updated, and remind them of the benefits of doing so.
- Making it easy for employees to install updates by scheduling the updates for non-working hours.
- Sending notifications when updates are available and reminding employees to install the updates.
- Motivation: employees need to see the value in keeping their applications and systems up to date, such as improved security and performance. The company can communicate this value proposition and the risks of not doing it. Increase motivation by:
- Showing the employees how keeping their applications and systems updated can help them to be more productive, by providing a secure way to use their tools, and by reducing the time and effort required to troubleshoot and fix issues arising from out-of-date systems.
- Nudges:
- Showing the employees the number of security vulnerabilities that have been fixed by updates in the past, or incidents avoided.
- Showing a progress bar or similar visual representation of the progress made on updating the systems and apps, to give employees a sense of accomplishment.
- Using anchoring, by offering different options for how updates are installed (e.g. automatic vs manual) and positioning the option that requires the least amount of effort as the best.
Measure#
What gets measured get managed. If you design an awesome strategy and don’t measure to verify its effectiveness, you’re shooting in the dark. Some good metrics for measuring security behaviour change are:
- Differentiated click-through rates (e.g. by psychological tactic)
- Reporting rate
- Time to report
- Skill level (across various topic areas)
- Risk reduction (e.g. are human-related security incidents going down?)
For some good ideas on security behaviour metrics, check out CybSafe’s How to use data to make your organisation more cyber secure whitepaper.
Security Culture#
Peter Drucker said “culture eats strategy for breakfast”. Having a solid behaviour change strategy is nothing without a good security-focused culture. Otherwise, the culture may work against the proposed behaviour change intervention strategy and have unintended effects. For example, a company which values productivity over security could result in a conflict of goals for employees, who end up being less security-compliant) than expected.
When an organisation has a strong cyber security culture, its employees are more aware of the importance of cyber security in the workplace and are more likely to act securely. However, creating and maintaining a positive security culture can be difficult as it’s deeply ingrained in an organisation’s overall culture and is influenced by various factors such as its mission, strategy, practices, and communication. Additionally, different subcultures may exist within the organisation across different locations. Efforts to change the culture may fail when trying to impose a new security culture on an existing one. It’s more effective to align the security culture with the existing culture rather than trying to change it.
And as I mentioned in the Assumptions section, having a cyber security culture can increase an employee’s motivation to have better cyber security habits to feel and show that they belong in that culture. It also increases social opportunities to behave more securely if more peers are doing the same, similar to peer pressure.
Negative Culture Trumps Everything#
Assessing an organisation’s security culture is crucial for evaluating its overall risk level. Even if individuals have knowledge and a favourable attitude towards security, a negative culture of mistrust, individualism, or unrealistic expectations can lead to insecure behaviour - instead of employees wanting to please and show they belong in the culture, they might be motivated to do the opposite and cause security incidents.
It won’t matter how much effort you put into your behaviour change strategy. If there’s a negative workplace culture you won’t change people’s motivations and security isn’t your biggest problem at that point.
Final Thoughts and Limitations#
All this may sound good in theory, however the proposed behaviour change intervention strategy is not applicable in all companies and all situations. Due to its complexity and big number of variables such a behaviour change intervention strategy can be very difficult to implement.
It will heavily depend on company size, culture, budget and resources, values and goals, senior management focus and personal agendas. It will also depend on technical aspects such as specific application features, configuration and customisation options, and the organisation’s technical capability to configure and customise these apps - for example, to produce helpful security tips and pop-ups when needed based on specific prompts, measuring how many people use certain software such as a password manager, and pushing specific app configs to employee devices en-masse.
For individuals and small companies (especially in New Zealand context) these behaviour change strategies are probably less applicable. So…
A Paradigm Shift is Needed#
The story is not over yet. Security behaviour change strategies may be the latest and coolest methods to manage human risk, using cutting-edge behaviour science and psychology. But…
All security behaviour change and influence strategies are addressing the symptom - when end users interact with technology there is a high probability of security incidents occurring. THIS IS NOT THE MAIN PROBLEM. The main problem is that none of these strategies are addressing the real cause - most insecure digital tech is rooted in the Supply Chain source, from its design to its implementation. These strategies are far too complex to apply to individual users and small businesses, and too late down the line. Perhaps these behaviour change strategies are put to better use at the source - where software is developed.
More on this in a future post…
Disclaimer#
The information in this article is provided for research and educational purposes only. Aura Information Security does not accept any liability in any form for any direct or indirect damages resulting from the use of or reliance on the information contained in this article.
